At its core, Data Leak Prevention (DLP) is a set of practices and tools designed to ensure your sensitive information stays where it belongs: inside your company. Think of it as a smart security guard for your data, preventing critical files from being accidentally or maliciously shared outside your network. For a growing SMB or startup, this isn't just a technical control; it's a critical strategy for protecting intellectual property, customer data, and meeting compliance obligations like ISO 27001, SOC 2, and DORA.
What Is DLP and Why It Matters for Your Business

Picture your company’s crown jewels: your customer lists, proprietary source code, financial reports, or strategic roadmaps. These aren't just documents; they're the lifeblood of your business. A DLP data leak prevention strategy acts as the guardian for these assets, constantly watching all digital exits to ensure nothing important walks out the door without the right permissions.
For small businesses and startups, protecting this data isn't just good practice—it's a matter of survival. A single, unintentional leak can trigger a cascade of disastrous consequences. The pain isn't just potential fines; it's about the very viability of your business.
The Real Cost of a Data Leak
When sensitive data gets out, the fallout can throw your entire company off course. The damage is far more than an IT headache; it hits your revenue, reputation, and future prospects, creating painful, immediate problems.
- Halted Sales Cycles: Potential customers, especially enterprise clients, will not partner with a company they see as a security risk. A data leak evaporates deals overnight and grinds your sales pipeline to a halt, directly impacting revenue.
- Destroyed Customer Trust: In business, trust is everything. Once it's gone, winning it back is a monumental task. Customers will flee if they believe their personal information isn't safe with you, and a damaged reputation can kill future growth.
- Blocked Funding Rounds: Investors do their homework. Any sign of a past data leak or a weak security posture is a massive red flag that can easily lead them to pull their funding offers, jeopardizing your company's future.
In short, a data leak broadcasts a message of immaturity and a lack of control. It undermines the confidence that customers and investors need to have in your ability to operate responsibly. This perception can be even more damaging than the breach itself.
From Cost Centre to Sales Enabler
This is where we need a mindset shift. For any growing business, a solid DLP plan isn’t just another expense on the balance sheet. It’s a strategic investment that fuels growth. A strong DLP programme can turn your security from a defensive cost into a proactive tool for winning business.
When you can demonstrate robust data protection, you build a foundation of trust that makes answering tough security questionnaires from big clients a breeze. This proactive stance is a core part of modern security, which you can read more about in our guide to Privacy by Design. Instead of scrambling to prove you’re secure after the fact, you have the policies and evidence ready to go, helping you accelerate procurement and close bigger deals, faster.
Understanding the Core Types of DLP Solutions

Putting a DLP data leak prevention strategy in place isn't about deploying a single, monolithic tool. An effective approach means choosing the right security for the right part of your business. Think of it like assigning different security guards to specific posts; you wouldn't put a lobby guard in charge of the server room. Each DLP solution is specialized to protect data wherever it lives and moves.
By understanding these functional categories, the entire concept becomes less intimidating. You can pinpoint exactly which solution addresses your company's most pressing risks and invest resources wisely to protect what matters most.
H3: Network DLP: The Border Patrol
Network DLP solutions are your digital border patrol. They sit at the edge of your network, monitoring all data leaving the organisation—whether through email, web applications, or file transfers. Their main job is to inspect network traffic in real-time to spot and block any unauthorised transmission of sensitive information.
For example, imagine a developer trying to email a snippet of proprietary source code to a personal account. A Network DLP tool would analyze the email's content, recognize the code as sensitive intellectual property, and block the message before it ever leaves your servers, preventing a critical IP leak.
H3: Endpoint DLP: The Device Guardian
Endpoint DLP zeroes in on the data stored, used, and moved on individual devices like laptops, desktops, and mobile phones. Software agents are installed directly onto these endpoints, giving you control over actions like copying data to a USB drive, printing a confidential document, or uploading files to an unsanctioned cloud storage service.
This has become absolutely crucial in the modern workplace. With the rise of remote work, endpoint DLP is a front-line defense against both accidental leaks and insider threats. This is a critical control for compliance frameworks like ISO 27001 and NIS 2. Platforms like Compli.st help you manage these controls, saving up to 90% of the effort on vendor security questionnaires and empowering you to close compliance gaps swiftly. For more detail, you can find further insights on the DLP solutions market on Data Insights Market.
H3: Cloud DLP: The SaaS Protector
As more businesses shift operations to the cloud, protecting data within SaaS applications like Microsoft 365, Google Workspace, and Salesforce has become a top priority. Cloud DLP solutions are built for this environment, integrating directly with cloud services via APIs to enforce security policies where your data now lives.
A common—and costly—mistake is an employee accidentally setting a shared folder of customer contracts and pricing sheets to "public" in Google Drive. A Cloud DLP tool would detect this misconfiguration, automatically revert the sharing setting to "private," and alert the security team, preventing a major data breach.
This type of DLP is essential for any startup or SMB that relies on cloud infrastructure, ensuring that convenience doesn't come at the cost of security.
H3: Data Discovery: The Census Taker
Before you can protect your sensitive data, you first have to know where it is. Data Discovery tools are the foundation of any strong DLP strategy. They act like a census taker, systematically scanning all your data repositories—servers, cloud storage, databases, and endpoints—to find, classify, and tag sensitive information.
This process is critical. It creates a comprehensive map of your "crown jewels," allowing you to apply targeted protection policies precisely where they're needed most. Without discovery, your DLP efforts are like trying to guard a vault without knowing what's inside or where all the doors are.
Comparison of DLP Solution Types
| DLP Type | Primary Focus | Common Use Case | Best For Protecting |
|---|---|---|---|
| Network DLP | Data in motion across the network | Monitoring and blocking sensitive data in emails, web traffic, and file transfers (FTP/SFTP). | Data leaving the organisational perimeter. |
| Endpoint DLP | Data in use on devices | Preventing data from being copied to USBs, printed, or moved from laptops and desktops. | Data on employee workstations, whether in-office or remote. |
| Cloud DLP | Data in the cloud (IaaS/SaaS) | Enforcing policies in cloud apps like Google Workspace, M365; preventing public sharing of sensitive files. | Data stored and shared within sanctioned cloud services. |
| Data Discovery | Data at rest everywhere | Scanning file servers, databases, and cloud storage to find and classify PII, IP, and financial data. | Unknown or unclassified sensitive data across the entire organisation. |
Ultimately, choosing the right DLP solution—or, more likely, a combination of them—depends entirely on where your sensitive data resides and how your teams use it. A layered approach is almost always the most effective.
How DLP Technology Actually Works
To really get a feel for what DLP data leak prevention can do, it helps to look under the hood. Let’s break down how these systems intelligently spot and protect your most sensitive information. It’s not magic; it’s a smart combination of detection methods that work in concert, creating a sophisticated defense rather than just a blunt blocking tool.
At its heart, DLP technology relies on a few key techniques to tell the difference between confidential data and everyday chatter. Once you understand these, you'll see how a good solution can make smart, informed decisions to keep your business secure.
Content Analysis: The Spell-Checker
The most direct method is content analysis. You can think of it like an advanced spell-checker. Instead of looking for typos, it scans files, emails, and messages for specific patterns or keywords that scream "sensitive data."
This approach is brilliant at catching structured data. For example, you can set it up to recognize and flag things like:
- A 16-digit sequence that looks exactly like a credit card number.
- National identification numbers or other forms of personally identifiable information (PII).
- Specific keywords you've defined, such as "Confidential," "Internal Use Only," or the codename for a top-secret project.
So, when an employee tries to email a spreadsheet packed with customer credit card numbers, the content analysis engine spots the pattern instantly and can block the email, based on the rules you’ve put in place.
Contextual Analysis: The Detective
While content analysis looks at what the data is, contextual analysis is more of a detective. It focuses on the circumstances surrounding the data transfer, asking critical questions to figure out if an action is suspicious, even if the content itself doesn't trigger a specific rule.
This method looks at the metadata and the environment, considering factors like:
- Who: Is this user even authorized to handle this type of data?
- What: What's the file type and size? Why is an executable file being sent from the finance department?
- Where: Where is the data headed? Is it being uploaded to a personal cloud storage account or sent to an unknown email address?
- When: Why is a huge amount of data being transferred well outside of normal business hours?
For instance, imagine someone from marketing tries to download your entire customer database at 3 AM and upload it to their personal Dropbox. Contextual analysis would immediately flag this as highly abnormal and risky behavior, even if no specific keywords were detected in the files themselves.
Data Fingerprinting: The Unique Signature
When it comes to protecting specific, highly sensitive unstructured documents, data fingerprinting is an incredibly powerful tool. It works by creating a unique digital signature—a "fingerprint"—of a critical file, whether that’s your company’s secret formula, a key legal contract, or your proprietary source code.
This fingerprint is essentially a precise hash calculated from the document's content. The DLP system stores this signature and constantly scans outbound data for a match. If even a snippet of the fingerprinted document shows up in another file or email, the system will recognize it and apply the right policy. This means the original document is protected even if it’s renamed or copied into a different file.
Machine Learning: The Anomaly Spotter
Finally, modern DLP solutions are increasingly leaning on machine learning (ML) to sharpen their detection skills. An ML engine learns the normal patterns of data movement across your organization, establishing a baseline for what "normal" looks like for each user and department.
Once that baseline is set, the system can instantly spot anomalies—actions that deviate from typical behavior. This allows it to catch new or sophisticated threats that might slip past pre-written rules, making your DLP data leak prevention strategy smarter and more resilient over time.
Building Your DLP Strategy From the Ground Up
For a startup or small business, implementing a full-scale DLP data leak prevention programme can feel overwhelming. But here's the good news: you don't need a huge budget or a dedicated security department to get started. By taking a practical, step-by-step approach, you can build a solid defense by tackling your biggest risks first.
The key is to see DLP as an ongoing process, not a one-off project. Start small, aim for wins that make a real difference, and let your strategy evolve as your business grows. This mindset makes effective data protection an achievable goal for any organization.
Step 1: Identify Your Crown Jewels
Before you can protect your data, you have to know what's truly worth protecting. The first order of business is to pinpoint the information that, if leaked, would be catastrophic for your business. These are your "crown jewels."
This critical data often includes:
- Proprietary source code or intellectual property (IP)
- Customer lists and personally identifiable information (PII)
- Financial records and sensitive pricing strategies
- Strategic business plans or investor-related documents
Pinpointing these assets is the bedrock of your entire strategy. It ensures you're focusing your energy and budget where it counts, which is a foundational requirement for frameworks like ISO 27001.
The core function of any DLP technology revolves around this very process: scanning for sensitive information, analyzing it, and creating a unique identifier or "fingerprint" for it.
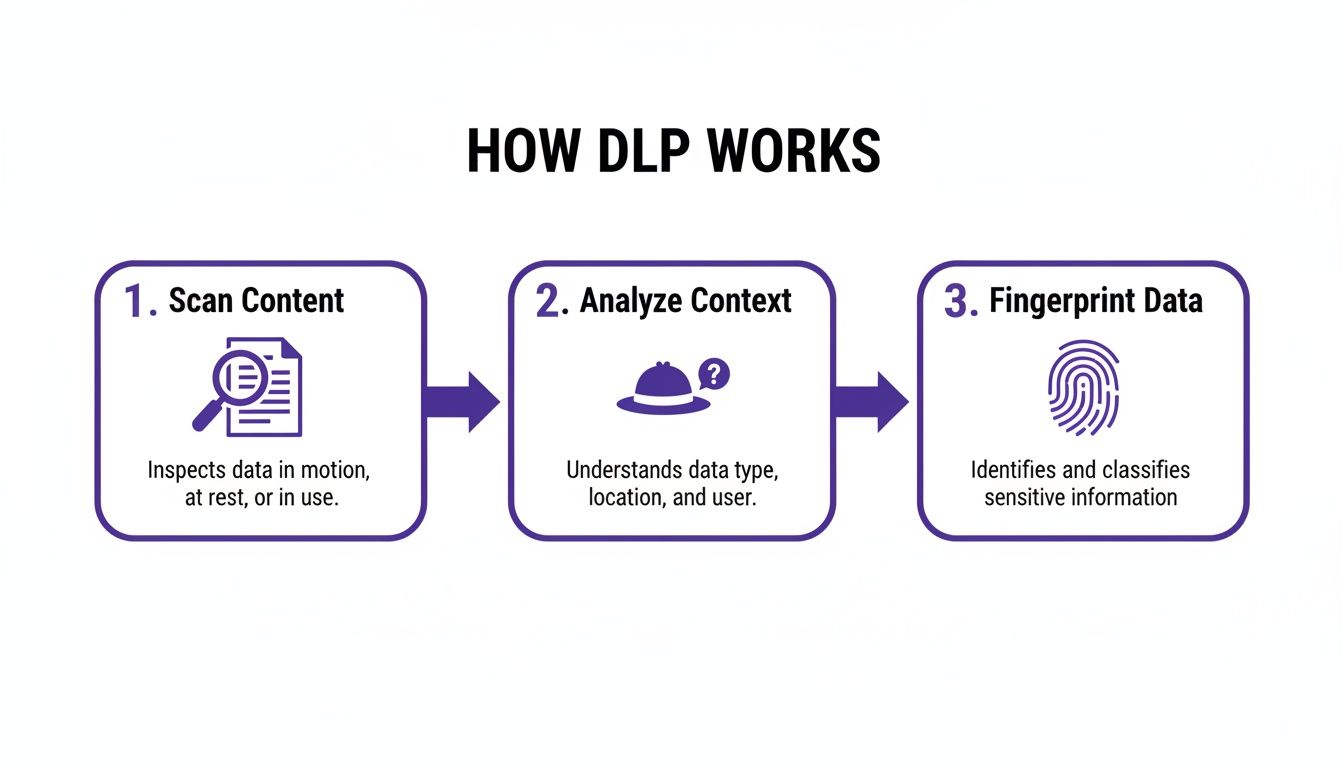
This diagram breaks down how DLP solutions work to identify and safeguard your most important information. It’s a methodical process of scanning content, understanding its context, and uniquely flagging your most critical files.
Step 2: Classify and Tag Your Data
Once you’ve identified your sensitive data, the next logical step is to classify it. You don't need a complex, multi-layered system right out of the gate. A few simple, intuitive tags that everyone in the company can understand will do the job perfectly.
A straightforward classification scheme could be as simple as this:
- Public: Information that can be shared freely.
- Internal-Only: Data meant for employee eyes only.
- Confidential: Highly sensitive information with restricted access.
- Restricted: Your most critical data, accessible to only a handful of people.
Applying these tags makes your data machine-readable. This is what allows your DLP tool to automatically and accurately enforce the rules you set, a key control in frameworks like SOC 2 and ISO 27001.
Step 3: Craft Smart, Simple Policies
With your data identified and classified, it’s time to write the rulebook. Your first DLP policies should be crystal clear, targeted, and focused on stopping the most common and damaging leaks. Resist the urge to create dozens of complicated rules at the start.
Start with high-impact policies that address obvious risks. A great first rule is to block any file tagged as 'Confidential' from being uploaded to personal cloud storage or sent to an external email address.
That one policy alone can prevent a massive range of accidental data leaks. As your program matures, you can layer in more nuanced rules. When you're ready to get more specific, a practical resource like this real-world data loss prevention email setup guide can provide actionable steps.
Step 4: Empower Your Team Through Training
Technology alone can't stop every data leak. Your employees are your first and best line of defense, and they need to be part of the solution. This doesn't mean you have to subject them to long, boring training sessions.
Instead, conduct brief, engaging training that focuses on practical skills and responsible data handling. Show them why classifying data matters and how their daily actions contribute directly to the company's security. A team that understands the 'why' is far less likely to make a costly mistake.
Step 5: Monitor, Refine, and Iterate
Finally, implementing DLP data leak prevention is not a "set it and forget it" task. Your business, your data, and the threats you face are always changing. That’s why it's absolutely vital to regularly check your DLP system's alerts and reports.
Use this feedback to fine-tune your policies. Are some rules generating too many false positives? Have new types of sensitive data emerged that need classifying? By treating your DLP strategy as a living process, you ensure it stays effective and aligned with your business for the long haul.
Turning Compliance from a Burden into an Advantage
For most growing companies, compliance frameworks like ISO 27001, SOC 2, and DORA can feel like an anchor. The requirements are dense, the process is time-consuming, and it often feels like a distraction from running the business. But what if you could flip that narrative?
A solid Data Loss Prevention (DLP) system is your secret weapon. It’s more than a security tool; it's a powerful engine for proving you're serious about protecting data. When auditors or enterprise clients come knocking, you're not left scrambling for evidence. You have logs, policies, and reports that demonstrate control in black and white.
How DLP Maps Directly to Compliance Controls
Auditors don't just want promises; they want to see technical measures in action. They are specifically looking for proof that you have mechanisms to prevent the unauthorized disclosure and leakage of information. A DLP solution is tailor-made to provide exactly that.
Here’s how it lines up with key compliance frameworks:
- ISO 27001: The framework is built on data classification and handling. Control A.8.2, "Labelling of Information," is the starting point for any DLP strategy. More broadly, the entire standard is about preventing data leakage. Our guide on ISO 27001 Annex A controls digs deeper into these requirements.
- SOC 2: This framework is all about the Trust Services Criteria. CC7.1, in particular, focuses on restricting access to sensitive information. DLP is the technology that enforces those restrictions, stopping classified data from ending up in the wrong hands.
- GDPR, NIS 2, & DORA: These regulations come with serious teeth, mandating strict protection of personal and operational data. DLP provides the technical muscle to enforce these rules, and just as importantly, generates the reports you need to prove due diligence and avoid heavy fines.
From Compliance Drudgery to a Sales Superpower
Here's where it gets interesting. The real value of a well-documented DLP system shows up when a big potential client sends over their security questionnaire. These documents are notorious for grinding sales cycles to a halt.
But with a DLP strategy in place, you already have the answers. Your data classification policies, incident reports, and monitoring logs are exactly what's needed to respond with confidence. Suddenly, compliance isn't a cost center; it's a sales enabler. You can showcase a mature security posture that builds trust and sets you apart from the competition.
The evidence your DLP system creates can be repurposed to conquer security questionnaires automatically. This transforms a defensive compliance task into a proactive tool that speeds up procurement and helps your sales team close deals faster.
This is precisely what platforms like Compli.st were built for. Our AI-powered system can take your DLP documentation and other security policies and generate accurate, evidence-backed answers in minutes. It effectively turns your compliance work into an always-on knowledge base that lets your sales team fly through security reviews.
The numbers back this up: 78% of companies seeking SOC 2 and ISO 27001 certifications use DLP solutions. The result? They cut their audit prep time by 45% and avoid 60% of potential penalties.
Completing the Data Protection Lifecycle
Great data security doesn't stop with monitoring active systems. Your compliance obligations cover the entire data lifecycle, from creation to destruction.
Beyond active prevention, you need to think about what happens when data is no longer needed. Auditors for frameworks like ISO 27001 and GDPR will verify that you have proper disposal practices. Implementing secure data destruction methods is the final piece of the puzzle. Combining secure disposal with your DLP strategy creates a complete, cradle-to-grave approach that protects information at every stage and makes your compliance position virtually bulletproof.
Choosing the Right DLP Solution for Your Startup
Finding the right DLP data leak prevention tool for a startup isn’t about ticking boxes on a feature list. It’s about finding a partner that fits your culture—powerful enough to protect you but simple enough that it doesn’t become a full-time job to manage. For a small, fast-moving business, the focus has to be on ease of use, smooth integration, and policies that can adapt as you grow.
The last thing you need is a platform that requires a dedicated engineer just to keep the lights on. You're looking for a solution your current team can roll out and manage without getting bogged down, freeing them up to focus on what they do best.
Look Beyond the Price Tag
The initial price of a DLP solution rarely tells the whole story. What you really need to consider is the Total Cost of Ownership (TCO), which includes the hidden costs of implementation, training, and day-to-day management. A seemingly cheap tool that requires constant babysitting will end up costing you far more in lost productivity and engineering time.
Instead, prioritize solutions that deliver on:
- Quick Implementation: Can you get it running in days, not months? Look for clear documentation and intuitive setup guides.
- Simple Policy Management: Your policy engine needs to be flexible enough to address your unique risks but straightforward enough that you can create and tweak rules without hiring a specialist.
- Seamless Integrations: A DLP tool is only as good as its ability to connect with the apps your team lives in every day, like Slack, Google Workspace, or Microsoft 35. If it doesn’t integrate properly, you’ll be left with blind spots.
Structuring a Meaningful Proof of Concept
A Proof of Concept (POC) is your chance to see how a solution performs in your world. Don't let a vendor walk you through a polished, generic demo. Instead, design a test that mirrors the actual challenges your startup faces.
For your POC, focus on a high-impact scenario. For instance, set up a policy to block any file containing the phrase "Project-Phoenix-Financials" from being shared in a public Slack channel. This gives you a true feel for the tool’s real-time monitoring and integration capabilities in a way that’s directly tied to your business risk.
This hands-on testing is invaluable. It cuts through the marketing fluff and shows you what the tool can really do before you sign a contract.
Key Questions to Ask Vendors
When you get on a call with a vendor, have a few sharp questions ready. This helps you get straight to the point and figure out if their solution is a good match for a startup.
- What’s the typical onboarding time for a company our size? This will give you a realistic idea of the implementation effort required.
- How does your solution handle false positives? A tool that’s too aggressive can bring work to a halt. You need a system that’s smart enough to be tuned, minimizing unnecessary alerts.
- Can you show us the integration with our key SaaS applications? Make them demonstrate how their tool connects with your specific tech stack, not just a generic one.
The threat of a data leak is always evolving. A staggering 55% of recent data breaches were linked back to unmonitored cloud apps that had no real DLP controls. This shows how critical these solutions are, especially for SaaS companies. You can explore the research on data loss prevention here to see more market trends.
Today, strong security isn't just a good idea—it's a requirement to win deals. Platforms like Compli.st are designed for this reality, helping you build a public Trust Center that can cut down on incoming security questionnaires by up to 70% and prove to clients that you take their data seriously.
Frequently Asked Questions About DLP
Getting started with DLP (Data Leak Prevention) can bring up a lot of questions, especially for startups and small to medium-sized businesses. Let's tackle some of the most common ones to help you understand how DLP fits into your security puzzle.
What Is the First Step in a Startup DLP Programme?
The absolute first step is to figure out what data you have and where it is. You can't protect what you don't know exists. This initial phase is all about data discovery and classification.
Start by identifying your "crown jewels"—the information that would be most damaging if it got out, like source code, sensitive customer data (PII), or financial forecasts. Once you know where this critical data lives, you can start labeling it with simple tags like 'Confidential' or 'Internal-Only'. This groundwork is essential for creating DLP policies that actually work and is a core requirement for ISO 27001.
How Does DLP Differ from a Firewall?
It's a common point of confusion, but they serve very different, complementary purposes. A firewall is like a bouncer at the door of your network. It checks IDs (like IP addresses and ports) to decide who gets in and out, but it doesn't care what they're carrying.
A DLP solution, on the other hand, is like a security guard inside the building who inspects the contents of every package leaving the premises. It's content-aware. It looks inside files and messages to see if they contain sensitive information and stops them from being sent to unauthorized places.
Here's a simple way to think about it: A firewall checks the envelope's address to see if it can be sent. DLP opens the envelope to read the letter inside and decides if the contents are too sensitive to leave the building.
Can DLP Prevent All Data Leaks?
In a word, no. No single tool can. A well-implemented DLP solution dramatically lowers the risk of data getting out through digital channels, whether by accident or on purpose. It’s brilliant at stopping someone emailing a customer list to their personal account or uploading a sensitive document to an unapproved cloud service.
However, DLP can't stop a determined person from taking a photo of their screen with their phone. That's why DLP must be one part of a bigger security picture. It needs to work alongside strong access controls, regular employee training, and a company culture that takes security seriously. Think of DLP as your most powerful technological safeguard for enforcing data policies automatically, not an infallible force field.
Ready to turn your DLP evidence into a sales advantage? Compli.st uses AI to automate security questionnaires, helping your team fly through procurement and close deals faster. Stop answering the same questions and start building trust. See how it works at Compli.st.