An ISO 27001 audit is an independent review of your company’s Information Security Management System (ISMS). For a growing startup or SMB, this process can feel like a major roadblock—complex, time-consuming, and expensive. But what if you viewed it not as a test to pass, but as a strategic tool to solve major business pain points? The audit validates your commitment to protecting sensitive data, giving clients and partners the proof they need to trust you.
For startups and SMBs, the real goal is simple: close bigger deals, faster. An ISO 27001 audit is the key to unlocking that growth.
ISO 27001 Audit At a Glance
| Component | Purpose for Startups & SMBs |
|---|---|
| ISMS Review | Verifies your security policies aren't just theoretical but are designed to solve real-world business risks. |
| Evidence Collection | Proves your security controls are actively working, turning your promises into tangible, auditable proof. |
| Interviews | Confirms your team understands their security responsibilities, demonstrating a strong, security-conscious culture. |
| Certification Decision | The final step that validates your security posture, providing a certificate that eliminates security blockers in enterprise sales cycles. |
This process might seem daunting, but it's one of the most effective ways to build a foundation for secure, sustainable growth and stop losing deals over security concerns.
Why Your First ISO 27001 Audit Is a Strategic Advantage

For a growing startup or small business, facing your first ISO 27001 audit can feel like a huge resource drain. The process looks complex and seems to demand time and money you don't have. But shifting your perspective from a compliance hurdle to a strategic asset changes the entire game. The real pain point isn't the audit; it's the stalled deals and endless security questionnaires from enterprise prospects.
Achieving ISO 27001 certification is one of the best ways to build immediate trust and open up new business opportunities. Enterprise clients often see it as a non-negotiable requirement, making it an incredibly powerful tool for your sales team.
Building Trust and Unlocking Growth
An ISO 27001 certificate is a universal language for security. It instantly tells potential partners that you are dedicated to protecting their information. This is especially vital when you’re handling sensitive client data or targeting highly regulated industries.
The audit process itself forces you to establish and document strong security controls, which naturally minimises risk and makes your business more resilient.
This structured approach delivers actionable business benefits:
- Accelerates Sales Cycles: Stop getting stuck on security objections. Answer lengthy security questionnaires in a fraction of the time and move deals forward.
- Enhances Customer Confidence: It proves you’re committed to data protection, giving you a real competitive edge against less mature competitors.
- Meets Regulatory Demands: It helps align your organisation with major regulations like GDPR, NIS 2, and DORA, preventing costly fines and opening doors in regulated markets.
The true value of an ISO 27001 audit isn't just the certificate. It's the disciplined, security-first culture you build—a culture that protects your business, unblocks enterprise sales, and proves to customers that their data is safe with you.
Responding to Regulatory Pressures
The demand for better data protection isn't just a market trend; it's increasingly written into law. The introduction of the GDPR was a perfect example, acting as a massive catalyst for security certifications across Europe. In 2018, France saw the number of ISO 27001 certifications triple—a surge directly linked to GDPR enforcement, as companies sought to demonstrate their due diligence.
While ISO 27001 gives you a complete framework for information security, other standards like SOC 2 Type 2 reports offer a different, yet complementary, approach. These focus more on how well your controls operate over time. Understanding both can help you build a robust compliance strategy that satisfies a wider range of customer requirements.
Ultimately, preparing for and passing an ISO 27001 audit sets your startup on a path for sustainable growth and long-term success.
Internal vs External Audits Explained

To get your head around the ISO 27001 certification journey, you first need to understand its two distinct audit types: internal and external. Each plays a critical role, and knowing how they work together is key to building a robust Information Security Management System (ISMS) and sailing through the certification process without costly surprises.
Think of it like preparing for a major stage production. The internal audit is your dress rehearsal. It’s your chance to find and fix mistakes before the paying audience arrives. The external audit? That’s opening night, when the official critics from an accredited body arrive to give their formal verdict.
A solid internal audit program isn't just a "nice-to-have"—it's a mandatory requirement under Clause 9.2 of the standard. More importantly, it’s your secret weapon for a successful external audit, letting you find and fix problems long before they can put your certification at risk.
The Role of the Internal Audit
An internal audit is essentially a systematic self-check to see if your ISMS is actually working the way you designed it to. The main objective is to get an impartial look at your security controls, policies, and procedures to make sure they're meeting both ISO 27001 requirements and your own business goals.
The process involves digging into your documentation, talking to your team, and testing whether your controls are effective. It's all about proactively hunting for "non-conformities"—the gaps where what you're doing doesn't match what the standard (or your own policy) says you should be doing.
Here are the actionable outcomes you're aiming for:
- Verify Compliance: Confirm your ISMS aligns with the ISO 27001 standard.
- Identify Weaknesses: Pinpoint vulnerabilities or process gaps before an external auditor finds them.
- Drive Improvement: Use what you learn to make meaningful fixes and strengthen your overall security posture.
- Demonstrate Due Diligence: Show everyone, from stakeholders to external auditors, that you're actively managing and improving your ISMS.
A well-executed internal audit is proof that your organisation is committed to continuous improvement, which is the core principle of the ISO 27001 framework.
The External Audit: Two Stages to Certification
When your internal audits show you're ready, it's time to call in the professionals. The external audit is performed by an independent, accredited auditor and is always split into two key phases.
Stage 1 Audit: The Documentation Review
The Stage 1 audit is a "desktop review." The auditor pores over your ISMS documentation to ensure all the foundational pieces are in place. They’re checking to see if your policies, scope, and procedures are clearly defined and actually line up with the standard.
Think of this as the auditor reviewing your playbook before the game. They’ll be looking closely at your Statement of Applicability (SoA), risk assessment methodology, and the overall ISMS framework to make sure your strategy is sound. If they find any major holes here, you'll need to patch them before moving on to Stage 2.
Stage 2 Audit: The Implementation Check
This is where the rubber meets the road. In the Stage 2 audit, the auditor moves beyond paperwork to verify that your ISMS isn’t just a theory—it’s fully functional and embedded in your organisation. This is a much more hands-on assessment, involving interviews with your team, observing processes, and reviewing hard evidence.
The Stage 2 audit is all about testing the reality of your security practices. The auditor's mission is to gather enough evidence to confirm that your controls are consistently implemented and effective at managing the information security risks you’ve identified.
During this phase, the auditor will take samples to check if your controls are working as intended. For example, they might ask to see access control logs, pull employee training records, or walk through your incident response plan. A successful Stage 2 audit is the final step—it’s what earns you your ISO 27001 certification.
Mapping Your ISO 27001 Audit Timeline
Getting ready for an ISO 27001 audit is more than a technical task—it's a strategic project that demands careful planning. A common and costly pain point for startups is underestimating the timeline, leading to rushed work, stressed teams, and a failed audit.
Think of it less like a sprint and more like a marathon. Each stage builds on the one before it, giving you a solid foundation for your Information Security Management System (ISMS). Mapping out the journey from the very beginning helps you manage your resources, set realistic goals, and avoid last-minute panic. Let's walk through what this roadmap really looks like.
The Initial Preparation and Scoping Phase
Before you can implement a single security control, you need to draw the map. This first phase is all about defining the scope of your ISMS. You’ll have to decide which parts of your business—your processes, office locations, and technologies—will fall under the certification. This is a crucial decision, as it dictates the complexity and duration of the entire project.
This is also when your team will conduct the initial risk assessment, which is the absolute cornerstone of your ISMS. It involves digging into potential threats to your information and figuring out the potential damage they could cause. This foundational work typically takes between one to three months, but it sets the stage for everything that follows.
ISMS Implementation and Evidence Gathering
Once you’ve defined your scope and identified your risks, it’s time for the longest and most intense part of the journey: implementation. This is where you actually build and deploy the security controls needed to tackle the risks you’ve uncovered. This means writing policies, training your team, configuring systems, and introducing new security-focused processes.
A massive part of this phase is collecting proof that your controls are working. This isn’t a one-off task; it’s an ongoing effort that demonstrates your security program is mature and effective. The implementation period can vary wildly, but you should budget for six to twelve months, depending on your company’s size and complexity.
The certification journey in France typically spans 9-18 months: 3-6 months for preparation, 6-12 months for ISMS implementation, and 2-4 weeks for the two-stage audit, with extra time for any corrections. This thorough process is often driven by French-specific regulations and the need to align with GDPR, where penalties for non-compliance can reach up to €20M or 4% of turnover. You can discover more insights about certifications that work well in France from AFNOR.
Internal Review and Management Approval
With your ISMS up and running, it's time for a dress rehearsal. Before an external auditor ever sees your system, you must conduct a comprehensive internal audit and a formal management review. The internal audit is your chance to find any non-conformities, while the management review ensures your leadership team is actively involved and overseeing the ISMS.
These steps aren’t optional; they’re required by the standard for two critical reasons:
- Spot Gaps Early: It allows you to find and fix problems before they show up as official findings in your external audit.
- Show Commitment: It gives the external auditor solid proof that your ISMS is a living, breathing part of your company culture.
This critical internal check-up usually takes one to two months, which includes time to remediate any issues you uncover.
The Two-Stage External Audit
At last, you’re ready for the main event: the certification audit. As we’ve covered, this is a two-part process handled by an accredited certification body.
- Stage 1 Audit (1-2 weeks): The auditor reviews all your documentation to make sure your ISMS is designed to meet ISO 27001 requirements. It’s essentially a "readiness check."
- Stage 2 Audit (1-2 weeks): This is the deep dive. The auditor will test your controls, interview your team, and verify that your ISMS is fully implemented and working effectively in the real world.
After a successful Stage 2 audit, the auditor recommends your organisation for certification. The whole external audit process, from the first day of Stage 1 to getting that certificate in your hands, can take anywhere from four to eight weeks. This timeframe depends on the auditor's schedule and how quickly you can address any non-conformities they might find.
To give you a clearer picture, here’s a typical timeline for a startup going through the process for the first time.
Typical ISO 27001 Audit Timeline for a Startup
| Phase | Typical Duration | Key Activities |
|---|---|---|
| Preparation & Scoping | 1-3 Months | Define ISMS scope, conduct risk assessment, identify stakeholders, secure management buy-in. |
| ISMS Implementation | 6-12 Months | Develop policies & procedures, implement security controls, train employees, gather evidence. |
| Internal Validation | 1-2 Months | Conduct a full internal audit, hold a management review meeting, and remediate any findings. |
| External Audit | 4-8 Weeks | Undergo Stage 1 (documentation review) and Stage 2 (implementation & effectiveness) audits. |
| Remediation & Certification | 2-4 Weeks | Address any non-conformities found by the external auditor and receive the final certification. |
Remember, these are just estimates. A well-resourced team with strong leadership support and automation tools might move faster, while a more complex organisation might need more time. The key is to have a realistic plan.
Your Pre-Audit Preparation Checklist
Knowing the theory behind an ISO 27001 audit is one thing; putting it into practice is another. For many startups, the hardest part is figuring out where to start. This actionable checklist breaks down the pre-audit essentials into clear, manageable steps to build a solid foundation for a successful certification.
Moving from theory to action requires a clear roadmap. This timeline visualises the journey from initial prep work through to the final audit, helping you map out your key milestones along the way.
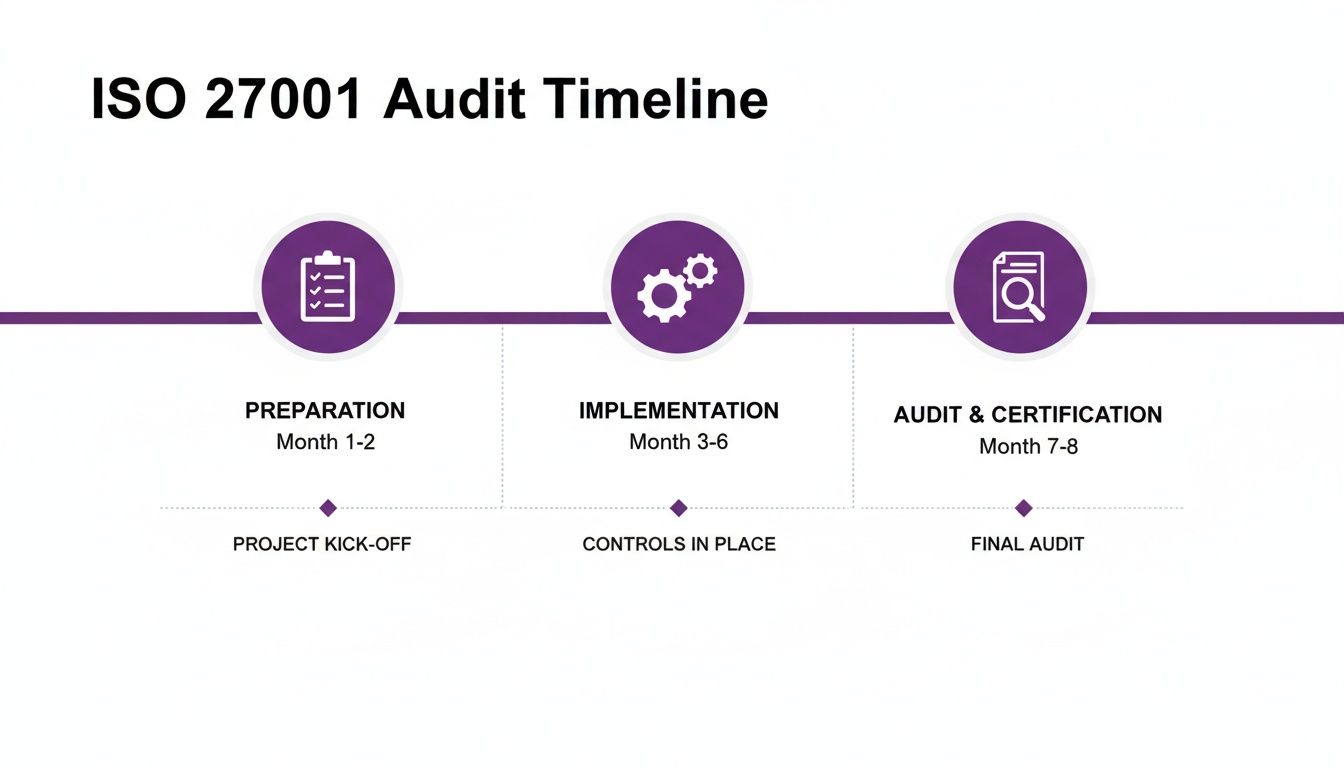
As you can see, preparation isn't just a quick first step. It's a significant phase that directly shapes how smoothly your implementation and the formal audit will go.
Define the Scope of Your ISMS
Before you can protect anything, you must be crystal clear on what you're protecting. This is why defining the scope of your Information Security Management System (ISMS) is always the first real step. This decision sets the boundaries for the entire audit and is a common failure point if done poorly.
Your scope needs to specify which parts of your organisation are covered. This includes departments, physical locations, assets, technologies, and key processes. A well-defined scope keeps you focused on what truly matters and prevents the dreaded "scope creep" that can derail an audit.
Conduct a Thorough Risk Assessment
With your scope locked in, it's time for the cornerstone of ISO 27001: a comprehensive risk assessment. This isn't just a box-ticking exercise. It's where you actively identify, analyse, and evaluate the security threats and vulnerabilities that could impact the assets and processes within your scope.
Think of it as creating a security roadmap. By understanding what could go wrong and how bad it could be, you can allocate your limited time and money where they'll have the most impact. The end goal is a clear picture of your risk landscape, which then feeds directly into your Risk Treatment Plan (RTP). This plan details exactly how you'll handle each risk—whether you decide to mitigate, accept, avoid, or transfer it.
Compile Essential ISMS Documentation
Auditors live on evidence, and your documentation is their primary source of truth. Well-organised, thorough documents prove that your ISMS is more than just an idea—it's a living system. The auditor will review these documents in depth during the Stage 1 audit to confirm you're ready to proceed.
Your core documentation package must include these key items:
- ISMS Scope Document: The official statement defining the boundaries of your ISMS.
- Information Security Policy: A high-level document showing management’s commitment to information security.
- Risk Assessment and Treatment Methodology: Your formal process for how you identify and manage risks.
- Statement of Applicability (SoA): A mandatory document that lists all applicable controls from Annex A, explains if they apply to your organisation, and justifies any exclusions.
The SoA is one of the most critical documents you'll produce. It connects the dots between your risk assessment findings and the security controls you've implemented, giving the auditor a clear rationale for your entire security strategy.
Remember, other regulations like GDPR also have strict documentation requirements. You can explore our detailed guide on the GDPR register to ensure your practices align with wider compliance needs.
Gather Evidence for Annex A Controls
Once your policies are written and controls are selected, you need to find tangible proof that they're actually working. This is the evidence the auditor will dig into during the Stage 2 audit to verify your implementation.
For every applicable Annex A control, you'll need to collect proof of its operation. This could be anything from:
- Access control logs and user access review records
- Reports showing who completed security awareness training
- Results from your latest vulnerability scans and penetration tests
- Minutes from management review meetings
- Records from incident response drills
ISO 27001 has seen significant growth in France, which issued its thousandth certificate by 2023. This trend is fuelled by frameworks like RGPD (GDPR) and NIS2, proving that a methodical approach to evidence collection is crucial in regulated markets.
Automating this process with a compliance tool can save you hundreds of hours. It transforms a painful manual task into a far more manageable, streamlined process.
How Automation Streamlines Your Audit
For startups and smaller businesses, the biggest hurdles in any ISO 27001 audit are almost always the same: not enough time, a tight budget, and too few people on deck. The old-school approach—drowning your team in endless spreadsheets, manual evidence gathering, and constant meetings—is a major pain point that drains resources, stalls innovation, and causes enormous stress.
There's a better way. Compliance automation platforms are built to transform this chaotic, labour-intensive project into a manageable, efficient workflow. They create a clear 'before and after' picture for your audit prep.

Imagine swapping scattered files for a central dashboard, replacing manual screenshots with real-time data feeds, and shifting from periodic checks to continuous monitoring. That's the power of automation, helping you get audit-ready faster and with significantly less friction.
From Manual Chaos to Automated Clarity
The manual road to an ISO 27001 audit is paved with repetitive, low-value tasks. Your team might spend weeks just chasing down proof of security controls, manually updating risk registers, and trying to align policies with how the business actually operates. It’s not just slow; it's incredibly prone to human error.
One simple request from an auditor can trigger a frantic search across multiple systems, pulling your valuable engineers away from building your product. This is precisely where compliance automation tools provide much-needed structure and efficiency.
A dedicated platform acts as a single source of truth for your entire Information Security Management System (ISMS). It provides a structured home where every policy, control, and piece of evidence is organised and linked, turning a chaotic scavenger hunt into a clear, auditable trail.
Automated Evidence Collection
One of the most gruelling parts of any audit preparation is gathering proof that your security controls are actually working. Manually taking screenshots of cloud configurations, downloading logs, and documenting user access reviews can easily consume hundreds of hours of your team's time.
Modern compliance platforms tackle this problem head-on by connecting directly to your tech stack.
- Cloud Service Integration: They plug into your cloud providers (like AWS, Azure, and Google Cloud) to automatically pull configuration data.
- Real-Time Monitoring: These tools continuously check settings to make sure they align with your security policies, like verifying that multi-factor authentication is enabled for all admin accounts.
- Automated Checks: They can automatically confirm that your backups are running, your data is encrypted, and your vulnerability scans are being performed on schedule.
This automated approach doesn't just save time—it provides much stronger, more reliable evidence for your auditor. Instead of presenting a static screenshot from three months ago, you can show a continuous, real-time record of compliance.
Pre-Built Templates and Policy Management
Drafting dozens of security policies from scratch is a massive undertaking, especially for teams without a dedicated compliance expert. You need policies for everything from access control and incident response to data retention and acceptable use.
A huge advantage of compliance tools is their library of pre-built, auditor-approved policy templates. These give you a solid foundation that can be customised to fit your business, saving countless hours of research and writing.
Beyond that, these platforms help you manage the entire policy lifecycle. They ensure policies are reviewed on a set schedule, track who has read and acknowledged them, and link each policy directly to the corresponding ISO 27001 controls. This creates a clear, defensible line between what your policies say and what you actually do. Choosing the right tool is key; you can find helpful information in our guide covering the 5 best Vanta alternatives and similar compliance solutions.
Streamlined Issue and Risk Management
No ISMS is perfect. During your prep, you'll inevitably find gaps or non-conformities that need fixing. Trying to manage these in spreadsheets is inefficient and makes it nearly impossible to track progress effectively.
Automation platforms centralise this entire process. When a control fails—say, a new cloud storage bucket is created without encryption—the system automatically flags it and creates a ticket. This ticket can then be assigned to the right person, given a priority level, and tracked right through to resolution.
This creates a complete, auditable record of your remediation work. When an auditor asks how you handle security weaknesses, you can show them a documented, systematic process for identifying, tracking, and fixing issues. It’s a powerful way to demonstrate a mature approach to continuous improvement. By automating these core tasks, you turn the audit from a painful, one-off project into a sustainable, ongoing security programme.
Common Questions About ISO 27001 Audits
Going through the ISO 27001 audit process for the first time brings up a lot of questions, especially for startups and SMBs focused on execution. Here are direct answers to the most common pain points and uncertainties.
How Much Does An ISO 27001 Audit Cost?
This is usually the first question, and the honest answer is: it depends. The cost of the external audit hinges on your company's size, complexity, and the scope you’ve defined for your Information Security Management System (ISMS).
As a rough guide, a smaller business with fewer than 50 employees can expect the external certification audit to fall somewhere in the €5,000 to €15,000 range for the initial three-year cycle.
However, this figure only covers the external auditor's time. The real pain point is the hidden cost: the internal resources spent on preparation, consultant fees, and lost productivity. This is where automation platforms deliver huge ROI. While they have an upfront cost, they drastically cut down on consultant hours and internal workload, helping you achieve certification faster and more cost-effectively.
What Is The Difference Between Non-Conformities?
During your audit, it's very likely the auditor will find "non-conformities"—the formal term for not meeting a requirement. They come in two flavours, and the difference is crucial.
- Major Non-Conformity: This is a critical system failure that puts the whole ISMS at risk. A classic example is failing to conduct a risk assessment at all. A major finding is a showstopper; it will prevent you from getting certified until you've fixed it and the auditor has verified the fix.
- Minor Non-Conformity: This is an isolated glitch that doesn't compromise the entire system. For instance, maybe a single new employee missed their initial security awareness training. You can still achieve certification with minor non-conformities, as long as you provide the auditor with a solid plan to correct them within a set timeframe.
The goal isn't to be perfect, but to demonstrate a robust system for identifying and fixing issues. A good ISMS is one that actively promotes continuous improvement, and your response to non-conformities is a key part of that.
Can We Get Certified Without An Internal Audit?
No. You absolutely cannot achieve ISO 27001 certification without conducting an internal audit first. Clause 9.2 of the standard is crystal clear: organisations must perform internal audits at planned intervals.
This isn't just bureaucratic red tape. The internal audit is your chance to find and fix issues before the external auditor does. More importantly, it provides the external auditor with concrete proof that you are actively monitoring, measuring, and improving your system's performance.
Trying to skip this step would earn you an immediate major non-conformity during your Stage 1 audit, stopping your certification process dead in its tracks.
How Do We Maintain Compliance After Certification?
Earning your ISO 27001 certificate is a massive achievement, but it’s not the end of the road. Certification marks the beginning of a continuous improvement cycle to keep your ISMS effective and your business secure.
To keep your certification active, you must perform these key activities regularly:
- Conduct Regular Internal Audits: You'll need to keep your internal audit programme running, typically at least once a year, to check the health of your ISMS.
- Hold Management Reviews: Your leadership team needs to meet periodically to review how the ISMS is performing, discuss risks, and assign resources where needed.
- Undergo Annual Surveillance Audits: The external auditor will be back. For the next two years, they’ll conduct smaller "surveillance audits" to ensure you're maintaining and improving your system.
This ongoing maintenance is a huge pain point for small teams. This is where compliance automation platforms become indispensable. They provide continuous visibility into your security controls, flag new gaps as they appear, and make gathering evidence for surveillance audits a simple task rather than a frantic annual project.
Ready to transform your compliance journey from a stressful project into a strategic advantage? Compli.st uses AI to streamline your entire ISO 27001 process, from automated evidence collection and risk assessments to completing security questionnaires in minutes. Discover how Compli.st can help you get audit-ready faster and with less effort.